When you hear the term “spoofed” email, does business email compromise (BEC) come to mind? It does for many people—especially security leaders. BEC is a form of email fraud, and it has been a top concern for chief information security officers for years.
BEC scams are a costly problem. The latest Internet Crime Report from the FBI’s Internet Crime Complaint Center (IC3) notes that adjusted losses from BEC were $2.9 billion last year. Since 2013, accumulated financial losses due to BEC have reached nearly $53 billion.
Spoofing is impersonation, and it is the essence of email fraud. It is also one of the most common techniques used in other types of attacks like phishing and ransomware. Your business, like many, probably focuses on stopping spoofed emails before they can reach employees’ inboxes. However, there is more to worry about. Spoofed email has the potential to damage your brand reputation and jeopardize your business ecosystem, too.
In this post, we will explore various impersonation risk scenarios. But first, let’s look at some common tactics.
Impersonation tactics
Here are some common methods bad actors use to impersonate others so they can further their attacks.
- Display name spoofing. The display name appears in the “From:” field of an email. It is the easiest email identifier to manipulate. Attackers forge email headers so that client software displays the fraudulent sender, which most users take at face value.
- Domain spoofing. Bad actors will use an exact match of an organization’s domain to launch this type of fraud attack. Attackers who engage in domain spoofing will attempt to imitate the sending server or sending domain.
- Lookalike domains. Third parties can register lookalike domains and send email that appears to have come from a trusted source.
- Compromised supplier accounts. In some advanced attacks, attackers will compromise an account from a supplier that works with the business that they want to target. They will use the compromised supplier account to hijack the email communication between their target and its supplier. Eventually, attackers are in a position to launch an attack or solicit fraudulent payment or sensitive data.
Attack scenarios
Now, let’s dive into how attackers can use spoofed emails to exploit the trusted relationships you have with your customers, business partners, suppliers and employees.
Scenario 1: Impersonate you to target your employees
You are probably most familiar with the first scenario, where attackers pretend to be someone within your company, like your CEO or manager. The scam often starts with a simple lure that seems to be a benign message like: How is your day? Are you at your desk? Can you help me with something urgent?
Once attackers get a victim to engage, the conversation evolves. The bad actor may request the victim to purchase gift cards for them, proceed with a fraudulent payment, or share confidential data.
Not only can attackers impersonate executives, but they can also pretend to be general employees asking human resources to redirect their payrolls. In short, it doesn’t matter what a victim’s role is. Anyone can be impersonated to target anyone within an organization.
An example of a simple lure where the attacker used display name spoofing to impersonate Ken, the CEO.
Proofpoint
Another example of a BEC lure where an attacker used a lookalike domain of Watertronics (vs. waltertronics, in the example) to spoof their CEO.
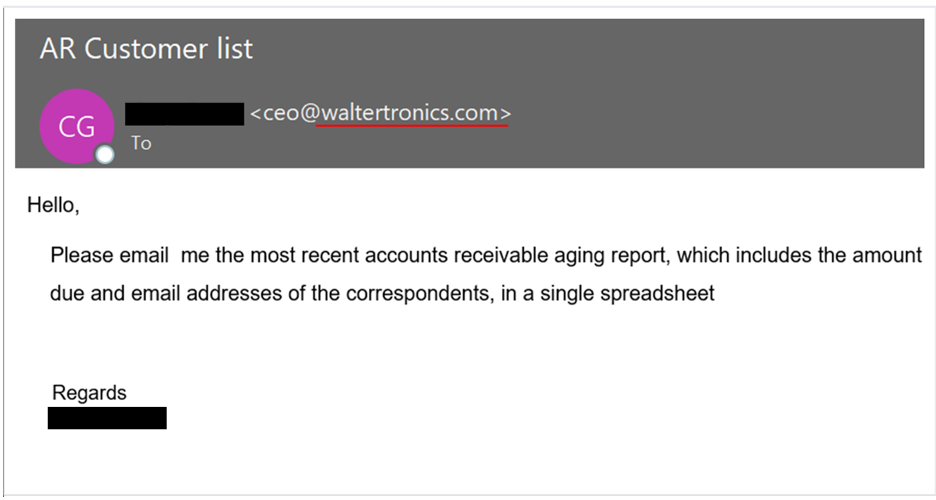
Proofpoint
Scenario 2: Exploit your suppliers or business partners to target your employees
The most common theme in this scenario is supplier invoicing fraud. Bad actors will exploit a company’s suppliers using tactics such as malicious lookalike domains of suppliers or compromised supplier accounts to either send a fake invoice or request the victim to redirect the payment to a bank account that the attackers control. (Sometimes, we see multiple tactics used jointly in a single attack!)
This approach targets business-to-business entities and can result in significant financial losses for those companies. It is not unheard of for businesses to lose tens of millions of dollars.
Compromised supplier accounts are hard to detect. Furthermore, adversaries can use this tactic in attacks other than BEC. For example, they can turn an invoice into a piece of malware and trick the victim into downloading a malicious attachment. Or they can obtain sensitive data from the victim who believes that they are interacting with a trusted vendor.
Regardless of the end game, attackers only have to intercept the business communications between you and your suppliers to achieve their goals.
An example where an attacker used a compromised supplier account to launch a supplier invoicing fraud attack.
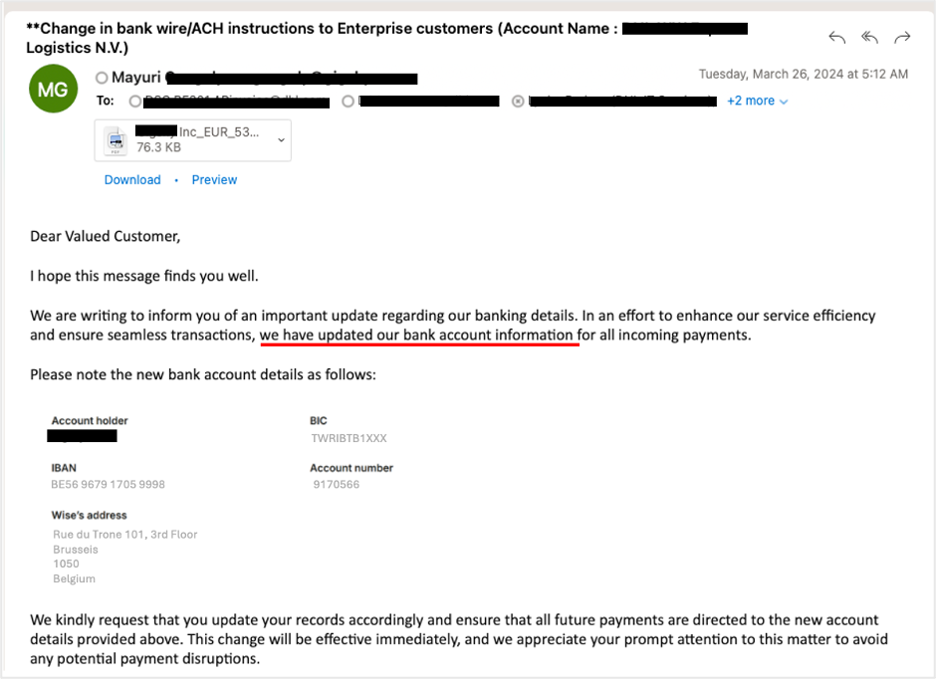
Proofpoint
Scenario 3: Impersonate you to target your business partners
Attackers can turn your suppliers against you—and they can turn you against your business partners. They do this by spoofing your trusted domains or by registering domains that look very similar to yours. Without proper controls in place, such as email authentication, your trusted domains are vulnerable to hijacking.
Unlike display name spoofing, domain spoofing is much harder to spot because the fraudulent email appears to come from a legitimate domain. At Proofpoint, we see about 23 million messages per day, on average, from unauthorized senders who potentially spoof trusted domains. And registering impostor domains could not be easier for attackers. Bad actors have registered as many as 300 impersonation domains in a single day to promote a phishing campaign.
A list of malicious lookalike domains registered by bad actors to impersonate PayPal, along with the date they were registered.
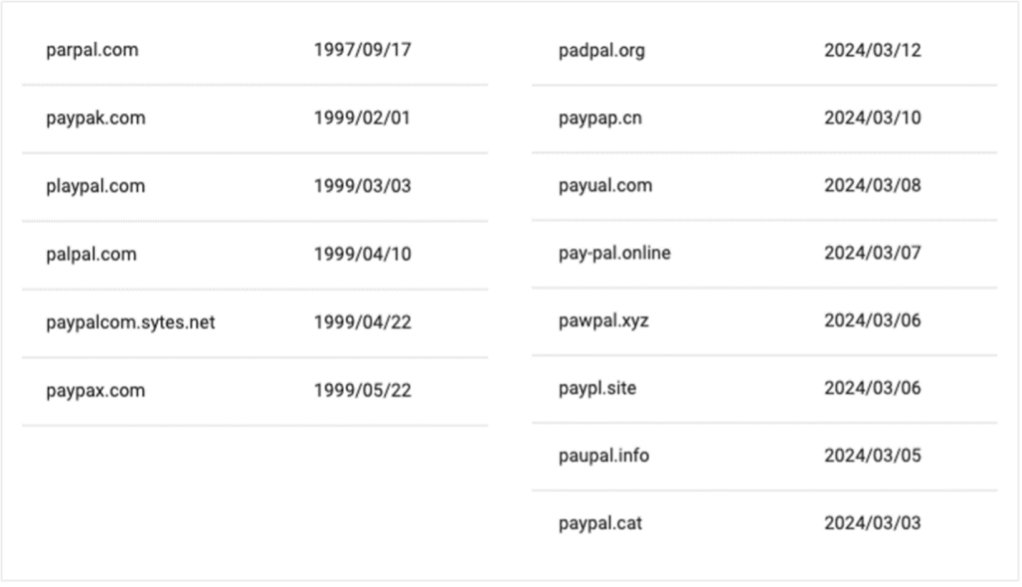
Proofpoint
Now you can start to see the complexity of impersonation risk. This is not just about threats that target your employees. These attacks could also impact your business negatively by damaging your brand and reputation. You don’t want to be considered a risky supplier by your business partners. And it is increasingly likely that your business partners will ask your business to implement controls that can prevent brand impersonation—if they haven’t done so already.
Scenario 4: Impersonate you to target your customers
Similar to the third scenario, attackers can impersonate you to target your customers, causing damage to your brand or reputation. It is critical to understand that bad actors not only can impersonate your user email, but also your application email. Many companies overlook this fact.
Compared with the number of transactional emails that applications generate, the number of user emails is like the tip of an iceberg. Moreover, you may have a high number of third-party apps, such as from software-as-a-service (SaaS) partners, sending transactional emails as “you” to your customers (and even to your employees). For example:
- A company might use Salesforce to send newsletters to customers
- Healthcare providers might partner with a SaaS vendor to send appointment reminders
- Merchants might use third-party apps to send order confirmation or shipping notifications
These emails are exposed to risk if they are not protected. Just like user email, application email can be spoofed. It can also carry a malicious payload if an attack compromises an app or a SaaS provider.
An example of an application-generated transactional email that was spoofed by attackers.
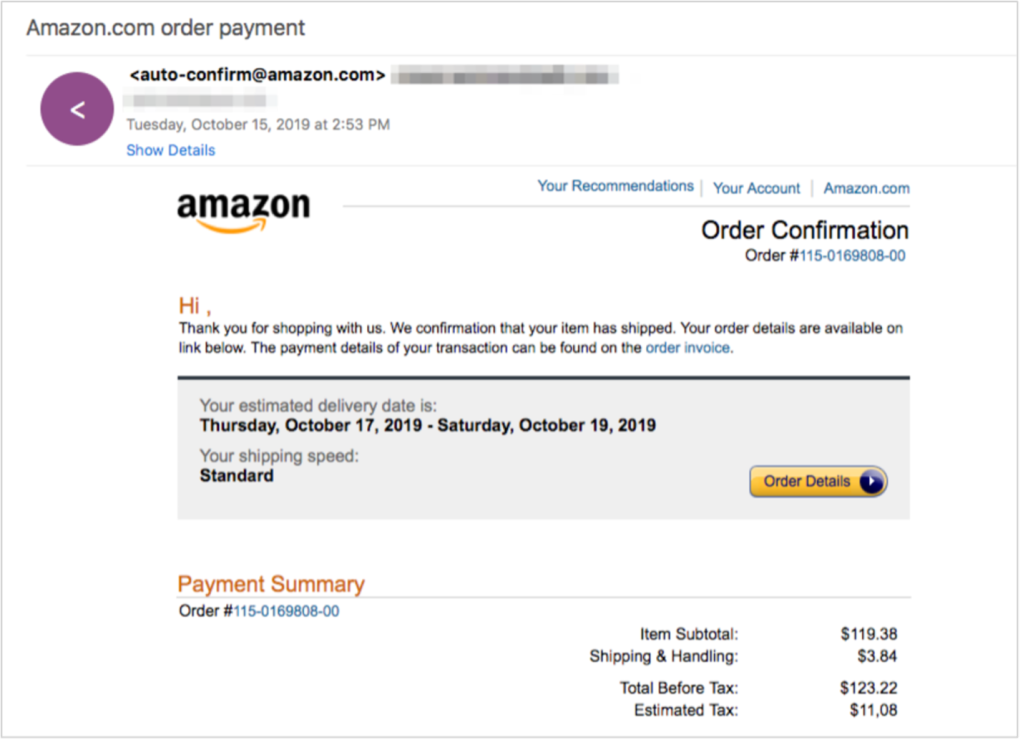
Proofpoint
Tips for mitigating your impersonation risk
Impersonation risk is a pervasive problem for every business. A multilayered approach to defense can help you reduce that risk. A robust email security solution will help you stop most threats before they can reach your end users’ inboxes. It can also detect and block a wide variety of threats that involve impersonation tactics, like phishing, malware, ransomware and BEC.
Here are some tips for finding the right solution and mitigating your risk:
- Look for advanced technology. To detect and block emerging threats more effectively, you need a modern email security solution that uses artificial intelligence and machine learning along with behavioral analysis, threat intelligence and even large language models (LLMs).
- Empower your employees. Since there is no single technology that can stop 100% of threats, it’s important to pair your threat detection solution with a threat-driven security awareness program. Doing so will give your employees the knowledge that they need to identify impersonation tactics and themes. Also, remember to give them tools to report any suspicious messages.
- Authenticate your emails. A critical aspect of impersonation risk is attackers spoofing your domain and abusing your brand and reputation. Email authentication is one of the most effective ways to prevent domain spoofing. So, look for a solution that can authenticate all your emails, including user and application emails.
- Get complete visibility, including compromised supplier accounts. The solution should provide you with complete visibility into any email sent as “you.” It should give you the confidence to enforce email authentication as well. When you have actionable visibility into compromised supplier accounts, you can better defend against sophisticated impersonation attacks where adversaries actually become your suppliers.
- Look for adaptive controls. Applying adaptive controls, like the isolation of URLs from risky suppliers, allows you to mitigate your exposure to compromised supplier accounts without disrupting your business.
Learn more
Proofpoint Impersonation Protection can help safeguard the trust between you and your customers, suppliers and business partners. It provides the most comprehensive protection for your trusted business communications against impersonation threats, with a multilayered defense.
To learn more, check out Proofpoint Impersonation Protection. And be sure to join our May 23 webinar, where our experts will engage in an in-depth discussion about impersonation threats.

