Yes, ladies and gents, we’re afraid it’s that time of the year month again. The time to peruse the list of apps installed on your Android device to try to spot malicious titles that might be out to get you.
More than 300,000 people could still be in danger
Now that’s a scary number, and the scariest thing might be the way these malicious Anatsa, Hydra, Ermac, and Alien campaigns were found to operate between the months of June and November of this year.
The truly devious nature of the newly unearthed banking trojans arises from their activation, which happened sporadically, cancelling out most of the red flags normally associated with this type of threat.
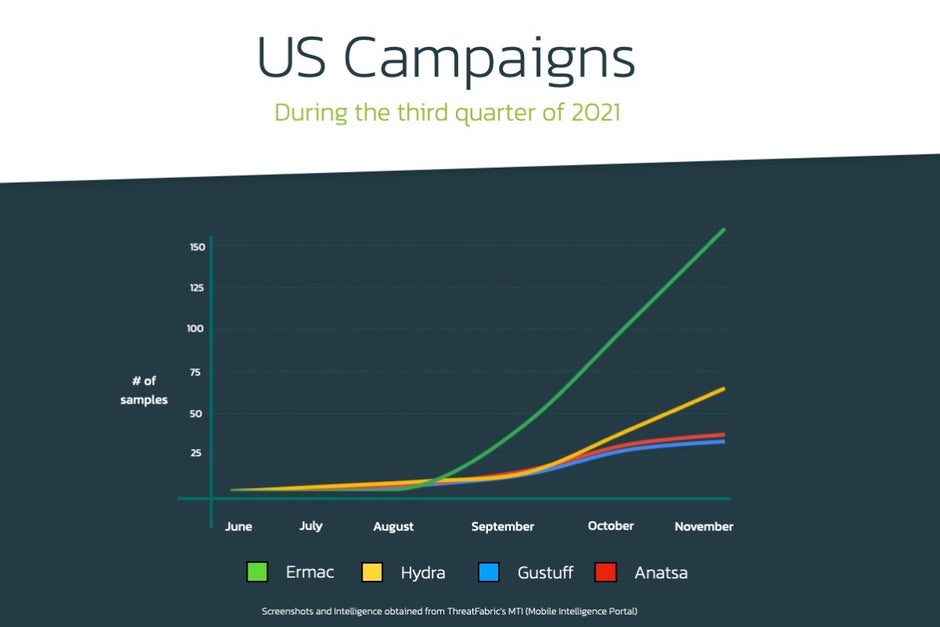
Otherwise put, not all users in all countries were attacked, and the ones who did become victims of the huge security breach were targeted at different times, as illustrated in the handy graph above. For many people, the malicious apps never stopped working as advertised, only occasionally asking for permission to install essential updates that were in fact trojan droppers.
Overall, it is estimated that more than 300,000 infections resulted from these widespread “campaigns” in four months, and while it’s not entirely clear how many of those users may still have their banking details at risk, you should probably take all the necessary precautions if you have reason to believe that might be the case.
This is the full list of malicious apps you need to delete ASAP
The first and most important security measure you have to employ as soon as possible, of course, is to uninstall these apps from your Android phone:
- Two Factor Authenticator (package name com.flowdivision)
- Protection Guard (com.protectionguard.app)
- QR CreatorScanner (com.ready.qrscanner.mix)
- Master Scanner Live (com.multifuction.combine.qr)
- QR Scanner 2021 (com.qr.code.generate)
- QR Scanner (com.qr.barqr.scangen)
- PDF Document Scanner – Scan to PDF (com.xaviermuches.docscannerpro2)
- PDF Document Scanner (com.docscanverifier.mobile)
- PDF Document Scanner Free (com.doscanner.mobile)
- CryptoTracker (cryptolistapp.app.com.cryptotracker)
- Gym and Fitness Trainer (com.gym.trainer.jeux)
- Master Scanner Live (leaf.leave.exchang)
- Gym and Fitness Trainer (gesture.enlist.say)
- PDF AI: Text Recognizer (com.uykxx.noazg)
- QR CreatorScanner (com.cinnamon.equal)
- QR CreatorScanner (com.tag.right)
Because some of the apps in question have incredibly generic, similar, or even identical titles, the package names should help you more easily distinguish them from the Google Play pack.
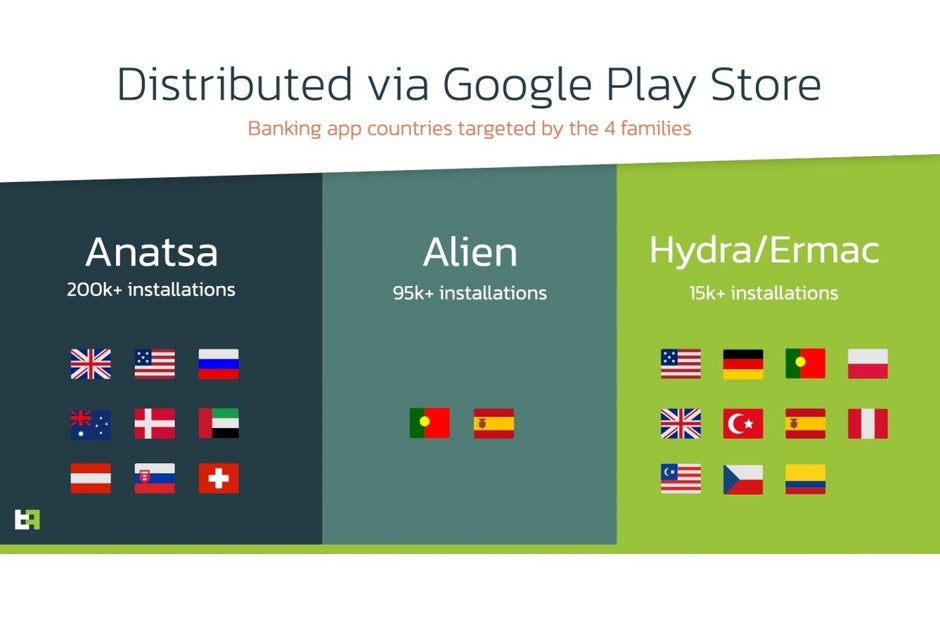
There’s a list of specific banks targeted by the Anatsa, Alien, Hydra, and Ermac trojans, by the way, but it’s far too long to copy and paste here, covering numerous top financial institutions across the old continent, Australia, Asia, and of course, the United States.
Of those generic-sounding apps, Free QR Code Scanner (from developer QrBarCode LDC) alone crossed the 50,000 install milestone before Google finally ejected it from the Play Store, so you might want to start your search there.
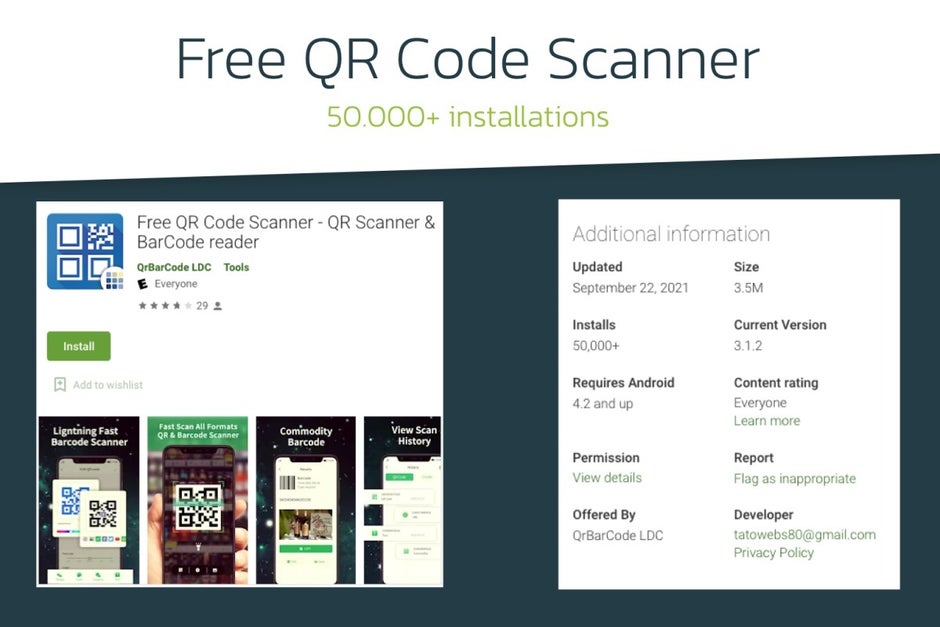
For what it’s worth, all of these particular apps have been removed from the official Play Store after their true intentions were discovered, but if history is any indication, it won’t be long until other bad actors are found.

