SquareX, an industry-first Browser Detection and Response (BDR) solution, leads the way in browser security. About a week ago, SquareX reported large-scale attacks targeting Chrome Extension developers aimed at taking over the Chrome Extension from the Chrome Store.
On December 25th, 2024, a malicious version of Cyberhaven’s browser extension was published on the Chrome Store that allowed the attacker to hijack authenticated sessions and exfiltrate confidential information. The malicious extension was available for download for more than 30 hours before being removed by Cyberhaven. The data loss prevention company declined to comment on the extent of the impact when approached by the press, but the extension had over 400,000 users on the Chrome Store at the time of the attack.
Unfortunately, the attack took place as SquareX’s researchers had identified a similar attack with a video demonstrating the entire attack pathway just a week before the Cyberhaven breach. The attack begins with a phishing email impersonating Chrome Store containing a supposed violation of the platform’s “Developer Agreement”, urging the receiver to accept the policies to prevent their extension from being removed from Chrome Store. Upon clicking on the policy button, the user gets prompted to connect their Google account to a “Privacy Policy Extension”, which grants the attacker access to edit, update and publish extensions on the developer’s account.
Fig 1. Phishing email targeting extension developers
Cyber NewsWire
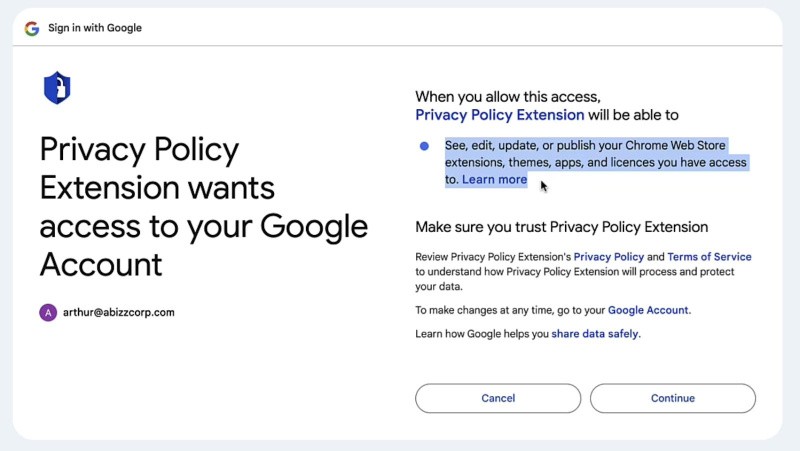
Fig 2. Fake Privacy Policy Extension requesting access to “edit, update or publish” the developer’s extension
Cyber NewsWire
Extensions have become an increasingly popular way for attackers to gain initial access. This is because most organizations have limited purview on what browser extensions their employees are using. Even the most rigorous security teams typically do not monitor subsequent updates once an extension is whitelisted.
SquareX has conducted extensive research and demonstrated at DEFCON 32, how MV3-compliant extensions can be used to steal video stream feeds, add a silent GitHub collaborator, and steal session cookies, among others. Attackers can create a seemingly harmless extension and later convert it into a malicious one post-installation or, as demonstrated in the attack above, deceive the developers behind a trusted extension to gain access to one that already has hundreds of thousands of users. In Cyberhaven’s case, attackers were able to steal company credentials across multiple websites and web apps through the malicious version of the extension.
Given that developer emails are publicly listed on Chrome Store, it is easy for attackers to target thousands of extension developers at once. These emails are typically used for bug reporting. Thus, even support emails listed for extensions from larger companies are usually routed to developers who may not have the level of security awareness required to find suspicion in such an attack. As per SquareX’s attack disclosure and the Cyberhaven breach that occurred within the span of less than two weeks, the company has strong reason to believe that many other browser extension providers are being attacked in the same way. SquareX urges companies and individuals alike to conduct a careful inspection before installing or updating any browser extensions.
Fig 3. Contact details of extension developers are publicly available on Chrome Store
Cyber NewsWire
SquareX team understands that it can be non-trivial to evaluate and monitor every single browser extension in the workforce amidst all the competing security priorities, especially when it comes to zero-day attacks. As demonstrated in the video, the fake privacy policy app involved in Cyberhaven’s breach was not even detected by any popular threat feeds.
SquareX’s Browser Detection and Response (BDR) solution takes this complexity off security teams by:
- Blocking OAuth interactions to unauthorized websites to prevent employees from accidentally giving attackers unauthorized access to your Chrome Store account
- Blocking and/or flagging any suspicious extension updates containing new, risky permissions
- Blocking and/or flagging any suspicious extensions with a surge of negative reviews
- Blocking and/or flagging installations of sideloaded extensions
- Streamline all requests for extension installations outside the authorized list for quick approval based on company policy
- Full visibility on all extensions installed and used by employees across the organization
SquareX’s founder Vivek Ramachandran warns: “Identity attacks targeting browser extensions similar to this OAuth attack will only become more prevalent as employees rely on more browser-based tools to be productive at work. Similar variants of these attacks have been used in the past to steal cloud data from apps like Google Drive and One Drive and we will only see attackers get more creative in exploiting browser extensions. Companies need to remain vigilant and minimize their supply chain risk without hampering employee productivity by equipping them with the right browser native tools.”
About SquareX:
SquareX helps organizations detect, mitigate, and threat-hunt client-side web attacks happening against their users in real-time.
SquareX’s industry-first Browser Detection and Response (BDR) solution, takes an attack-focused approach to browser security, ensuring enterprise users are protected against advanced threats like malicious QR Codes, Browser-in-the-Browser phishing, macro-based malware, and other web attacks encompassing malicious files, websites, scripts, and compromised networks.
With SquareX, enterprises can provide contractors and remote workers with secure access to internal applications, and enterprise SaaS, and convert the browsers on BYOD / unmanaged devices into trusted browsing sessions.
Contact
Head of PR
Junice Liew
SquareX
junice@sqrx.com
PostBlock
SquareX Researchers Expose OAuth Attack on Chrome Extensions Days Before Major Breach
Notice
Selecting a featured image is recommended for an optimal user experience.Set featured imageDo not show Featured Image on Post
Hide featured image for article details page
786 words, 4 minutes read time.
Last edited 34 minutes ago.
StatusDraft
PublishImmediately
Link/squarex-researchers-expose-oauth-attack-on-chrome-extensions-days-before-major-breach
Sticky
StickyEnable AMP
First PublishedJanuary 2, 2025 04:37 AMDisplay as Updated Article
Will display the updated flag on the article for readers.Article status:DraftReady for ReviewReady for PublishOn-HoldPublishUpdatedTrashPrimary Publication:NoneARNNETChannelAsiaCIOComputerSwedenComputerwocheComputerworldComputerWorld PolandComputerWorld SpainCSOOnlineInfoWorldITWorldNetworkWorldReseller
Suppress Monetization
Authors
Dibyoshnata TalukdarSelect An Author
Featured video
Set Video
Floating video
Indexing
Newsletter visibility
Redirect Link
Byline
Overrides any authors selected above, and allows authors to be added to BrandPosts
Author Bio Setting
Create Translated Post
Article Read Time
Story Types
Add New Story Type
Separate with commas or the Enter key.
Most used $s
- News
- Opinion
- Feature
- Analysis
- News Analysis
- How-To
- BrandPost
- Reviews
- Interview
- Tip
Article Types
Add New Article Type
Separate with commas or the Enter key.
Most used $s
- default
- external url
- news
- brandpost
- video
- Slideshow
- CIO
- featured
- Interview
- Profiles
Add New Sponsorship
Separate with commas or the Enter key.
Most used $s
- Innovating to transform
- Connected
- Interconnecting Business & Cybersecurity
- SD-WAN: Performance Matters
- The CIO Factor
- VMware Cloud Verified – Increasing your speed to cloud success
- Transform to a modern hybrid infrastructure
- Transform your data center to a modern hybrid infrastructure
- Defining the Future of Customer Experience Management
- Manufacturing Tech
Blogs
Add New Blog
Separate with commas or the Enter key.
Most used $s
- Layer 8
- InfoWorld Tech Watch
- Apple Holic
- Shark Tank
- Buzzblog
- Cisco Connection
- Seeing Through Windows
- Data Center Explorer
- Cloud Insider
- Alpha Doggs
Podcast series
Origin CMS
Categories
Toggle panel: CategoriesSelect Categories 1693 1699 1703 1705 1707 1714 1721 1722 1723 1731 1732 1735 1737 1738 1740 1742 1744 1750 1751 1752 1754 1756 1758 1759 1761 1765 1766 1767 1769 1770 1772 1779 1785 1794 1814 1827 1865 1956 1958 1966 1976 1978 1984 1986 1990 1992 2015 2016 2017 2018 2019 2022 2024 2031 2036 2038 2039 2041 2065 2066 2067 2071 2073 2076 2084 2087 2090 2091 2093 2101 2106 2108 2111 2126 2128 2129 2131 2136 2137 2138 2140 2146 2151 2161 2167 2169 2177 2178 2180 2181 2192 2193 2199 2200 2204 2205 2207 2215 2218 2219 2237 2249 2250 2251 2253 2260 2262 2273 2281 2287 2288 2295 2298 2304 2305 2308 2310 2311 2314 2318 2321 2322 2325 2326 2328 2331 2333 2336 2338 2347 2349 2359 2360 2362 2363 2369 2379 2381 2447 2460 2462 2472 2495 2526 2534 2540 2558 2568 2595 2602 2625 2632 3D Modeling Tools 3D Printers 4G 4k TVs 5790 5G 7750 802.11x 9261 Accenture Access Control Accounting Software Acer Action Cameras Active Directory Adobe Systems Advanced Persistent Threats Aerohive Aerospace and Defense Industry Africa Agile Development Agriculture Industry Akamai AKG Alcatel-Lucent Alexa Alibaba All-in-One PCs Alphabet Amazon Echo Amazon Prime Day Amazon re:Invent Amazon Web Services Amazon.com AMD Amplitude Analytics Android Android Auto Android Security Angular Anti Malware Antispam AOC Apache Apache Spark APIs App Testing Apple Apple App Store Apple Photos Apple TV Apple Watch Appliances Application Integration Application Life Cycle Management Application Management Application Performance Management Application Security ARM Artificial Intelligence Asia ASMedia ASML ASRock Asset Management Software Asus AsusTor AT&T Atlassian AU Optronics Augmented Reality Augmented Reality Devices Australia Australia and New Zealand Authentication AutoML Automotive Industry Avanade Avaya AWS Lambda Azure Functions Back to School Backup and Recovery Banking Batteries BBK Electronics Belkin BenQ Best Bets Beyond Big Data Bing Biometrics Bitbucket BitDefender Black Friday and Cyber Monday Black Hat BlackBerry Blockchain Blu-ray Drives Blue Coast Systems Bluetooth Botnets Box BPM Systems Broadband Brocade Brother Browser Security Browsers BTO Budget Budgeting Bugs Build Automation Burnout Business Business Analyst Business Continuity Business Intelligence Business Intelligence and Analytics Software Business IT Alignment Business Operations Business Process Management Business Relationship Manager Business Services C Language C-Suite C# C++ CA Cables Calendars Camcorders Camera Accessories Camera Lenses Cameras Canon Canonical CAO Capgemini Car Tech Careers CarPlay Carriers Cars Casio CCPA CDW Cellular Networks Central America CenturyLink CEO Certifications CES CFO CGI Group Change Management Channel Sales Chargers Chatbots Check Point Chief Data Officer Chief Digital Officer Children’s Tablets China Chrome Chrome OS Chromebooks Chromecast CI/CD Ciena CIO CIO 100 CIO des Jahres CIO Leadership Live Cisco Systems Citrix Systems Cloud Access Security Broker Cloud Architecture Cloud Computing Cloud Foundry Cloud Management Cloud Native Cloud Security Cloud Storage CM.com CMO Code Editors Collaboration Software Comcast Commercial Providers Communications Security Compliance Computer Accessories Computer Cases Computer Components Computer Networking Devices Computer Speakers Computer Storage Devices Computers Computers and Peripherals Concurrency Configuration Management Connected Devices Construction and Engineering Industry Consumer Electronics Containers Content Management Systems Converged Infrastructure COO Cooling Systems Cord Cutting Core Java Cortana CPUs and Processors Critical Infrastructure CRM Systems Cryptocurrency CSO and CISO CSO50 CTO Cyberattacks Cybercrime Dash Cams Data and Information Security Data Architecture Data Breach Data Center Data Center Automation Data Center Design Data Center Management Data Engineering Data Governance Data Integration Data Management Data Mining Data Privacy Data Quality Data Science Data Scientist Data Visualization Data Warehousing Database Administration Database Administrator Database Design Database Virtualization Databases DCIM Software DDoS Deco Deep Learning Dell Dell EMC Deloitte Design Patterns Design Thinking Desktop Linux Desktop NAS Desktop PCs Desktop Virtualization Developer Development Approaches Development Libraries and Frameworks Development Tools Devops DevSecOps Digital Leader Award Digital SLR Cameras Digital Transformation Digital Video Accessories Disaster Recovery Diversity and Inclusion Django DLP Software DNS Docker Docking Stations Document Databases Document Management Systems Drivers Drones Dropbox DVD Players DVR/PVR E-commerce Services E-commerce Software E-readers E3 eBay Eclipse Eclipse Foundation EDGE Edge Computing Education and Training Software Education Industry EIZO Election Hacking Electric Bikes Electric Cars Electric Scooters Electronic Health Records Email Clients Email Security Emerging Technology Employee Experience Employee Protection Encryption Endpoint Protection Energy Efficiency Energy Industry Engineer Enterasys Enterprise Enterprise Applications Enterprise Architecture Enterprise Buyer’s Guides Enterprise Mobile Management Enterprise Routers Enterprise Search Enterprise Storage Entertainment Software Epic Epson Ergonomics Ericsson Ernst & Young ERP Systems ETL Europe European Union Events External Hard Drives Extreme Networks F5 Facebook Facial recognition Feature Phones Federated Identity Felton Lantech File Sharing Film Finance and Accounting Systems Financial Services Industry Fintech Fire TV Firefox Firewalls Fiserv Fitness Devices Flash Storage FlexVirtual Fortinet Foundations and Projects Foursquare Foxconn Fraud Fraud Protection and Detection Software Fujitsu Functions as a Service G Data Cyberdefense G Suite Gadgets Galaxy Gamescom Gaming Gaming Accessories Gaming Chairs Gaming Laptops Gaming PCs Gaming Platforms GDPR Gear General Electric Generative AI Genesys Geography Germany Gigabyte Technology Gigamon GitHub GitLab Gmail Google Google Assistant Google Cloud Functions Google Cloud Next Google Cloud Platform Google Docs Google Drive Google Glass Google Go Google Home Google I/O Google Pixel Google Play Google Search Google Sheets Government Government IT GPS Trackers GPUs Graph Databases Graphic Design Tools Graphics Cards Green IT H-1B Visas Hacker Groups Hacking Hadoop Hamburger IT-Strategietage Hard Drives Harman International Harman Kardon HCL Technologies HDTVs Headphones Headsets Health and Beauty Tools Health and Fitness Software Healthcare Industry High-Performance Computing HIPAA Hiring Hitachi Holidays Home Audio Home Security HomePod Hotspots HP HP Enterprise Services HPE HR Director HRIS HTC HTML Huawei Hubs and Controllers Hulu Human Resources Hybrid Cloud Hybrid Laptops Hyperconverged Infrastructure Hypervisors IaaS IBM IBM Global Services iCloud ICT Partners Identity and Access Management Identity Management Solutions Identity Theft IDG Events IFA iiyama Illustration Software iMac Image Editors Image recognition Incident Response India Industry Infor Informatica Infosys Infrastructure Management Inkjet Printers Innolux Innovation Innovation Awards Input Devices Instagram Instant Cameras Insurance Industry Integrated Development Environments Intel Intellectual Property IntelliJ Internal Hard Drives Internet Internet Explorer Internet of Things Internet Security Internet Service Providers Intrusion Detection Software Investigation and Forensics iOS iOS Security IoT Platforms IoT Security iPad iPhone iPod IPv6 IT Consulting Services IT Director IT Governance IT Governance Frameworks IT i Vården IT Jobs IT Leadership IT Management IT Operations IT Skills IT Strategy IT Training ITIL ITSM iTunes Jakarta EE Japan Java Java ME Java SE Java Swing JavaScript JBL Joyent jQuery Julia Juniper Networks Kaspersky Lab Key Value Databases Keyboards Kindle Kingston Kotlin KPMG KPN Kubernetes Kyocera LaCie LAN Laptop Accessories Laptop Cases Laptop Security Laptops Laser Printers Latin America and the Caribbean Legal Lenovo Lexmark LG Chem LG Corp LG Display LG Electronics Life Sciences Industry Lifestyle Software Lighting Lightning LinkedIn Linksys Linux Linux Foundation LoB Manager Logitech LoRa Mac Mac Mini Mac Pro MacBook Machine Learning Machine Vision MacOS MacOS Security Mainframes Major Appliances Malware Managed Cloud Services Managed IT Services Managed Service Providers Manufacturing Industry Manufacturing Systems Maps and Navigation Software Mark Levinson Marketing Marketing and Advertising Industry Marketing Software Markets Master Data Management McAfee McKinsey Media and Entertainment Industry Medical Devices Memory Cards Mentoring Mergers and Acquisitions Meridian Mesh Wi-fi Routers Messaging Apps Messaging Security Mice Micro-Star International Microservices Microsoft Microsoft .NET Microsoft 365 Microsoft Azure Microsoft Edge Microsoft Excel Microsoft Exchange Microsoft Office Microsoft Outlook Microsoft PowerPoint Microsoft SharePoint Microsoft SQL Server Microsoft Surface Microsoft Teams Microsoft Word Mid-range Military Mimecast Mining, Oil, and Gas MMD Mobile Mobile Application Management Mobile Apps Mobile Development Mobile Device Management Mobile Management Mobile Payment Mobile Phone Accessories Mobile Phone Cases and Covers Mobile Phones Mobile Security Mobile World Congress MobileIron Monitors Motherboards Mozilla MPLS MU-MIMO Multi Cloud Multi-factor Authentication Multifunction Printers Music Music Players MySQL Natural Language Processing NBN NetApp Netbeans Netflix Netgear Netherlands NetSuite Network Administrator Network Appliances Network Architect Network Function Virtualization Network Management Software Network Monitoring Network Security Network Switches Network Virtualization Network-Attached Storage Networked Players Networking Networking Devices Neural Networks New Zealand NFC Nikon Nintendo Nintendo Switch No Code and Low Code Node.js Noise-cancelling Headphones Nokia Nonprofits Northern America NoSQL Databases NTT Nutanix Nvidia NVMe Object Storage Office Suites Offshoring Oki Okta ON2IT OneDrive Open Software Foundation Open Source OpenOffice OpenStack OpenText Operating Systems Oppo Oppo OnePlus Optical Drives Oracle Oracle Database Orange Cyberdefense Orbi Outsourcing PaaS Palo Alto Networks Panasonic Password Managers Passwords Patch Management Software Payment Systems PC Cooling PCI PDF Editors Penetration Testing Personal Databases Personal Software Philips Phishing Photo Printers Photography Photoshop PHP Physical Security Ping Identity Pinterest Pivotal PlayStation Plex Systems PLM Software Poly Ports PostgreSQL Power Supplies Power Systems Powerline Adapters Predictive Analytics Premium Pricing Printers Privacy Private 5G Private Cloud Process Improvement Procurement Software Productivity Software Professional Services Program Management Programming Languages Project Management Project Management Tools Project Portfolio Management Projectors PwC Python PyTorch Qualcomm Quality Assurance Quantum Computing R Language Rackspace Radware Ransomware Raspberry Pi Raspberry Pi Foundation React Realme Red Hat Regulation Relational Databases Relationship Building Remote Access Remote Access Security Remote Work Renewable Energy Resellers Resumes Retail Industry RFID RHEL Ricoh Risk Management Riverbed Robotic Process Automation Robotics ROI and Metrics Roku Roku Player Roles Routers RSA Conference RSA Security Ruby Rust SaaS Safari Salaries Salesforce Automation Salesforce.com Samsung Electronics SAN SAP SASE Scala Scanners Science Industry SD-Branch SD-WAN SDN Seagate SecaaS Security Security Audits Security Cameras Security Hardware Security Information and Event Management Software Security Infrastructure Security Monitoring Software Security Operations Center Security Practices Security Software Self-driving Cars Sensors Server Virtualization Serverless Computing Servers Service Management Software Service Mesh ServiceNow Set-top Boxes Sharp Shopping Shopping Occasions ShoreTel Short-range Wireless Single Sign-on Siri Slack Small and Medium Business Small Appliances Smart Appliances Smart Gardens Smart Heaters Smart Home Smart Speakers Smart TVs Smartphones Smartwatches Social Engineering Social Networking Apps Software Deployment Software Development Software Licensing Software Providers Solid-State Drives Sony Sound Cards South America South Korea SpaceX Speakers Splunk Sports Software Spotify Sprint SQL Staff Management Startups Steam Stereo Systems Storage Management Software Storage Security Storage Virtualization Streaming Devices Streaming Media Styluses Supercomputers SuperMicro Supply Chain Supply Chain Management Software Surveillance SUSE Sweden Swift SXSW Symantec System Administration System Integration System Management System Memory (RAM) Systemhauskongress Systems Integrators T-Mobile Tablet Accessories Tablet PCs Tablets Tata Consulting Services Tech Support Technology Industry Telecom Equipment Telecommunications Telecommunications Industry Telematics Telemedicine Telephony Television TensorFlow Tesla Texas Instruments Thermostats Threat and Vulnerability Management Tibco Toshiba Toys and Recreation TP Vision TP-Link TPV Technology Transaction Processing Transportation and Logistics Industry Travel and Hospitality Industry Travel Apps TV and Video TV Antennas TV Tuners TvOs Twitter Typescript Uber Ubuntu Ultrabook Ultraportable Laptops Uncategorized Unified Communications Unified Endpoint Management Unified Threat Management Unisys United Kingdom United States of America Unix USB USB 3 USB Flash Drives USB-C Utilities Utilities Industry Vacuums Veeam Vendor Management Vendors and Providers Venture Capital Verizon Verizon Media Group Version Control Systems Video Video Cameras Video Editors Video Games Video Players Videoconferencing Vine Virtual Reality Virtual Reality Devices Virtualization Virtustream Viruses Visual Basic Visual Studio Visual Studio Code Vivo VMware Vodafone Voice Assistants VoIP VPN Vue Vulnerabilities WAN WAN Optimization WatchOs Wearables Web Development Web Search Webcams Western Digital Wi-Fi Wii WIICTA Windows Windows 10 Windows 11 Windows Laptops Windows PCs Windows Security Windows Server Wipro Wireless Charging Wireless Headphones Wireless Security Women in IT Workday Workstations WWDC Xbox Xerox Xiaomi Corp Xirrus YouTube Zendesk Zero Trust Zero-day vulnerability Zigbee Zoom Video Communications ZTE
Toggle panel: TagsSelect Tags
Copyright info
Toggle panel: Copyright infoCopyright text
Given that developer emails are publicly listed on Chrome Store, it is easy for attackers to target thousands of extension developers at once. These emails are typically used for bug reporting. Thus, even support emails listed for extensions from larger companies are usually routed to developers who may not have the level of security awareness required to find suspicion in such an attack. As per SquareX’s attack disclosure and the Cyberhaven breach that occurred within the span of less than two weeks, the company has strong reason to believe that many other browser extension providers are being attacked in the same way. SquareX urges companies and individuals alike to conduct a careful inspection before installing or updating any browser extensions.
SquareX team understands that it can be non-trivial to evaluate and monitor every single browser extension in the workforce amidst all the competing security priorities, especially when it comes to zero-day attacks. As demonstrated in the video, the fake privacy policy app involved in Cyberhaven’s breach was not even detected by any popular threat feeds.
SquareX’s Browser Detection and Response (BDR) solution takes this complexity off security teams by:
- Blocking OAuth interactions to unauthorized websites to prevent employees from accidentally giving attackers unauthorized access to your Chrome Store account
- Blocking and/or flagging any suspicious extension updates containing new, risky permissions
- Blocking and/or flagging any suspicious extensions with a surge of negative reviews
- Blocking and/or flagging installations of sideloaded extensions
- Streamline all requests for extension installations outside the authorized list for quick approval based on company policy
- Full visibility on all extensions installed and used by employees across the organization
SquareX’s founder Vivek Ramachandran warns: “Identity attacks targeting browser extensions similar to this OAuth attack will only become more prevalent as employees rely on more browser-based tools to be productive at work. Similar variants of these attacks have been used in the past to steal cloud data from apps like Google Drive and One Drive and we will only see attackers get more creative in exploiting browser extensions. Companies need to remain vigilant and minimize their supply chain risk without hampering employee productivity by equipping them with the right browser native tools.”
About SquareX:
SquareX helps organizations detect, mitigate, and threat-hunt client-side web attacks happening against their users in real-time.
SquareX’s industry-first Browser Detection and Response (BDR) solution, takes an attack-focused approach to browser security, ensuring enterprise users are protected against advanced threats like malicious QR Codes, Browser-in-the-Browser phishing, macro-based malware, and other web attacks encompassing malicious files, websites, scripts, and compromised networks.
With SquareX, enterprises can provide contractors and remote workers with secure access to internal applications, and enterprise SaaS, and convert the browsers on BYOD / unmanaged devices into trusted browsing sessions.
Contact
Head of PR
Junice Liew
SquareX
junice@sqrx.com